This article is about Cyber Security
What is Cyber Security and how does it keep us safe?
By NIIT Editorial
Published on 09/01/2021
6 minutes
Cybersecurity is the combined practice of securing a business’s IT infrastructure that includes both intellectual property and assets such as computers, networks, and data from being accessed by unauthorized entities. The steps taken to ensure data integrity to mitigate internal theft or save hardware/software equipment from natural disasters are also classified under cybersecurity. It is comprised of the following sub-categories:
Application Security
Software is arguably the most critical component upon which the tech enterprises of the day rest. As a consequence of which the necessary steps to secure the application architecture are a must. The best practices to do so involve steps such as asset tracking, threat assessment, patching, container management, and encryption in a long list of to-dos. Privileges have to be managed for authorized on-premises data sharing and to avoid leaks.
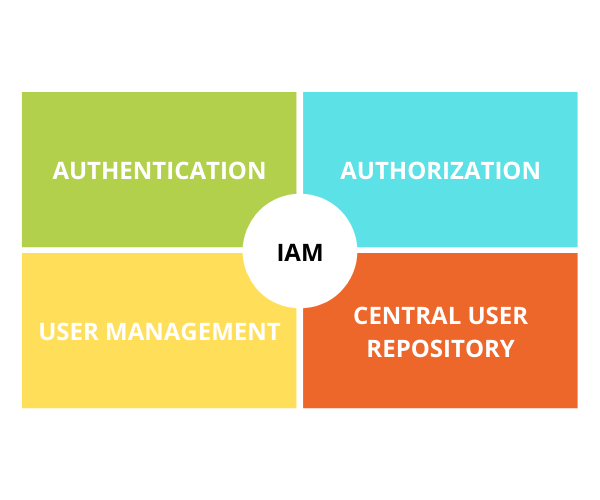
Identity & Access Management (IAM)
As the name suggests, it is the framework of activities that identify, legitimize and extend access to the information systems of an organization. There are 4 pillars of identity management namely authentication, authorization, user management, and central user repository. Adherence to IAM procedures ensures data integrity and contributes towards operational fluency preventing unwarranted data transits and offering data access to only those who must.
Network Security
The main objective of this sub-domain of cybersecurity is to protect information. Data leak prevention, digital fraud prevention, and security compliance management are the subject areas of network security. Some of the techniques employed to deal with external/internal data threats include dynamic application security testing, penetration testing, and static application testing.
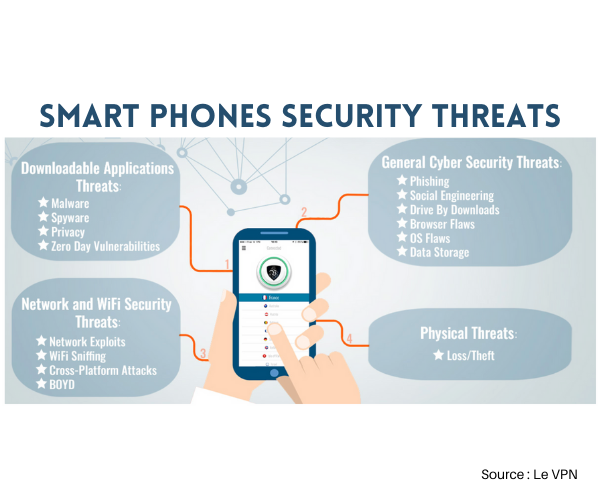
Mobile Device Security
There is no going about in the world without portable devices. Mobile security encompasses tablets, laptops, smartphones, and other carryable devices that need to be secured for data sharing. Enterprise security planning cannot be complete without ensuring the safety of mobile devices. Benchmark practices recommended for the same include end-to-end encryption, password protection, installation of relevant biometrics appliances, and enforcing clear directorates for the use of such devices within and outside the official premises.
Disaster Recovery
Calamities may not issue advance warnings before striking hard. In case of natural disasters, or man-made accidents loss of data could cause business-failings to arise sooner than later. Data recovery and business continuity planning involve identifying the scope of operations and inter-departmental dependencies, defining responsibilities, and laying out procedures to recover data after a downtime/crash as well as preparing backup alternatives.
Customer Awareness
It is important the end-user understands the significance and importance of the applications they are subject to. Enterprise workforce training for professionals to ensure the requisite knowledge transfer can clear the basic doubts related to identifying anomalous online activity. The variety and sophistication of cyber threats will continue to rise given how fast technology is evolving. It is only with timely knowledge that professionals can be made to understand the significance of cybersecurity.
Advanced Post Graduate Program in Cybersecurity & SecOps
StackRoute, an NIIT venture, has come up with yet another standout certification program for the masses. Just like its acclaimed engineering MOOCs, this one focuses on developing cyber instincts in both IT and non-IT professionals/learners. The applicants get a taste of on-the-job cyber security challenges, and are backed up with the promise of job assurance. This 18-week long outcome oriented program makes learners day-1 job-ready.
Apply now!
Advanced PGP in Cybersecurity and SecOps
Become an industry-ready StackRoute Certified Cybersecurity Analyst. This program transforms learners with no Information Technology background into cybersecurity specialists. This is a Job-Assured Program with a minimum CTC of ₹ 5LPA*
Job Assurance*
Flexible Payment Option
 Sign Up
Sign Up